
This simple hacked device can steal iPhone information
An ethical hacker made a device that impersonates an Apple product, for about sixty euros. Take the opportunity to try out hundreds of iPhones during a major trade show.
Def Con, the world’s largest hacker conference, has surprises in store every year. During the latest release, which took place in Las Vegas in August, an ethical hacker tried to connect to iPhones for several days in hotel lobbies and conference rooms.
Many attendees regularly received Apple TV connection requests on their smartphones, to the point of becoming a Def Con mystery on social media.
After confusing hundreds of people who didn’t understand where these pop-ups came from, cyber security expert Jay Buchs ended it up detects on August 13 on the social network Mastodon that it was behind these mysterious contact attempts.
Jay Bush said he ran this experiment for two reasons: to remind people to ” Really turn off bluetooth “because” It’s funny “.
Bluetooth is a bug in all devices
American media journalists Techcrunch They were able to interview the ethical hacker and ask him how he works. Jae Bochs built himself a device consisting of a Raspberry Pi Zero 2 W (nano computer), two antennas, a Bluetooth adapter, and a portable battery. The whole thing would have cost just over sixty euros (without the battery).
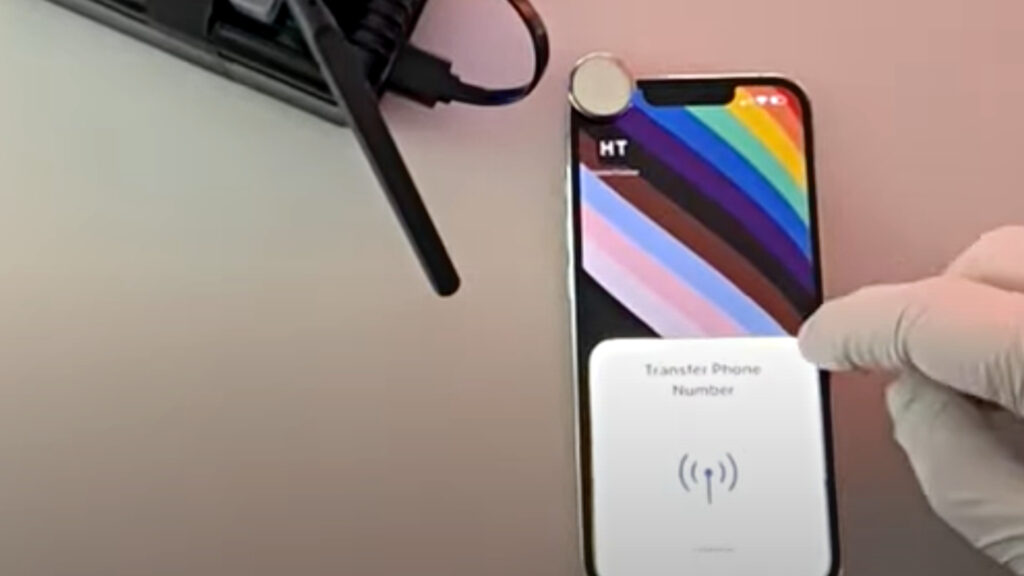
The electronic researcher then copied the signal that the Apple TV ad would cause, impersonating an Apple device repeatedly trying to connect to nearby devices. Jae’s device will then initiate connection requests to all nearby Apple products.
These issues have been known before, Jae Bochs said, at least since a 2019 academic paper that looked at Apple’s Bluetooth Low Battery protocol. Many defects leak information that can be retrieved via Bluetooth. The cyber expert indicated that he did not steal any data, but in another context, his device may trick the user into logging in. From there, the hacker can start extracting a lot of information.
As for Jae Boch, Apple should warn the user that pressing the Bluetooth icon doesn’t completely disable the option since the iPhone can still interact with proximity-activated tags, like his device.
Bluetooth hacks are regularly performed by internet experts. Researchers have already unlocked Teslas, connected locks, or medical devices from these flaws. However, such operations are still extremely rare. These hacks require you to be close to the target and have the necessary hacking tools.
participation in Numerama on Google News So don’t miss any information!

“Incurable web evangelist. Hipster-friendly gamer. Award-winning entrepreneur. Falls down a lot.”
