The Difference Between Cyber Security and Information Security: Everything You Need to Know
In today’s digital-first world, data is the new gold. But like gold, it needs protecting. Every day, individuals, businesses, and governments face increasing threats to their digital and physical information. While most people use the terms cyber security and information security interchangeably, they are not the same thing.
If you’re serious about protecting your data—whether you run a multinational corporation, a small business, or simply value your personal privacy—you need to understand the differences between these two fields.
This comprehensive guide will unpack cyber security and information security, explore where they overlap, and explain why understanding the distinction matters for you and your organisation.
1. The Basics: Defining the Two Terms
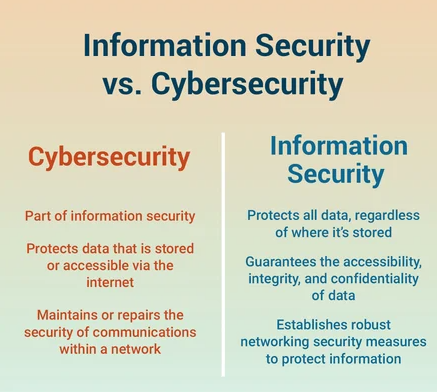
What is Cyber Security?
Cyber security refers to protecting systems, networks, devices, and data from unauthorised digital access, theft, or damage. It focuses mainly on the online and technological realm—the cyber world.
Core goals of cyber security include:
- Preventing hacking attempts and cyber attacks.
- Securing networks from malware, ransomware, and phishing.
- Protecting personal and organisational data from being stolen online.
Cyber security often deals with:
- Firewalls and intrusion detection systems.
- Encryption for data in transit and at rest.
- Authentication measures such as multi-factor authentication (MFA).
- Security patches and software updates.
What is Information Security?
Information security (often shortened to InfoSec) is broader than cyber security. It is the practice of protecting all forms of information—whether digital, physical, or even verbal—from unauthorised access, misuse, or destruction.
Key elements of information security:
- Covers both digital and physical security.
- Applies to printed documents, conversations, and even memory storage devices.
- Ensures the confidentiality, integrity, and availability of information (known as the CIA Triad).
For example:
- Locking sensitive paper files in a cabinet is information security.
- Encrypting an email is also information security—but now it overlaps with cyber security.
2. The Main Differences Between Cyber Security and Information Security
While they overlap significantly, the focus areas set them apart.
Aspect
Cyber Security
Information Security
Scope
Focuses only on digital/cyber threats.
Covers all information—digital, physical, or spoken.
Main Threats
Hackers, malware, phishing, ransomware.
Theft, espionage, natural disasters, insider threats.
Protection Medium
Networks, devices, and systems.
Information in all forms and locations.
Tools Used
Firewalls, antivirus, encryption, MFA.
Physical locks, access control, policies, AND cyber tools.
Goal
Protect the cyber realm.
Protect all forms of information assets.
3. Why the Confusion Exists
The confusion between the two terms comes from the fact that most information today exists in digital form—which means cyber security measures are often part of information security strategies.
For instance:
- If a company protects its customer database from hackers, that’s cyber security.
- But if it also protects the printed contracts in a locked office, that’s information security.
Many professionals use the terms interchangeably, but knowing the difference is important when planning security strategies, allocating budgets, or hiring specialists.
4. Examples to Clarify the Difference
Cyber Security Example:A hacker tries to break into a bank’s online system to steal customer login credentials. The bank uses firewalls, anti-malware software, and encrypted login systems to block the attack.
Information Security Example:The same bank also keeps physical copies of customer loan applications in locked filing cabinets, with restricted staff access, and requires visitors to sign in before entering secure areas.
Both aim to protect sensitive data, but cyber security works in the virtual space, while information security spans both the digital and physical worlds.
5. Why Both Matter in the Modern World
The explosion of remote work, cloud computing, and global connectivity means cyber threats are rising faster than ever. At the same time, insider threats, human error, and physical breaches still pose significant risks.
In reality, you can’t have one without the other:
- Cyber security protects your online assets.
- Information security protects everything—offline and online.
6. Overlapping Areas Between Cyber Security and Information Security
There’s significant overlap, and here’s where things can get tricky:
- Data encryption protects both online data and stored files.
- Access control systems work for both computer logins and physical building entry.
- Incident response plans apply whether you face a cyber breach or a theft of physical documents.
This is why many organisations integrate both under a single security strategy.
7. Real-World Industries Where the Difference Matters
Financial Institutions
Banks need to secure online transactions (cyber security) and physical records of client information (information security).
Healthcare
Hospitals must protect electronic health records (cyber security) while ensuring printed medical files are safe from unauthorised access (information security).
Online Entertainment
Streaming platforms protect user accounts digitally (cyber security) but also secure licensing agreements and contracts in physical form (information security).
8. The Role of Human Error
Studies consistently show that human mistakes are among the biggest security risks—regardless of whether it’s cyber or information security. Clicking a phishing link, misplacing a USB drive, or leaving sensitive papers on a desk can all lead to breaches.
That’s why security training is critical in both fields.
9. How “top casino bonuses in new zealand” Relates to Security Concepts
Even in industries you might not associate with data protection, like online casinos, cyber and information security are critical. The concept of top casino bonuses in new zealand is a marketing strategy, but behind the scenes, these platforms must secure player data, payment transactions, and promotional codes from hackers.
It’s a good reminder that security is universal—whether you’re in finance, healthcare, or online gaming.
10. Key Skills Needed in Each Field
Cyber Security Professionals
- Network and system security.
- Ethical hacking.
- Malware analysis.
- Cloud security.
Information Security Professionals
- Policy creation and enforcement.
- Risk assessment and management.
- Physical security controls.
- Legal compliance.
11. The Future of Cyber and Information Security
Emerging technologies like AI, blockchain, and quantum computing will reshape both fields. Cyber security will have to defend against smarter, faster attacks, while information security will need to evolve to protect data across both physical and digital spaces.
12. Final Thoughts
Cyber security and information security are like two sides of the same coin. One guards the digital gates, the other protects the entire kingdom. In today’s data-driven world, businesses and individuals need both to ensure their valuable information remains safe.
Understanding the difference is more than semantics—it’s the foundation of a strong, resilient security strategy.

“Incurable web evangelist. Hipster-friendly gamer. Award-winning entrepreneur. Falls down a lot.”
